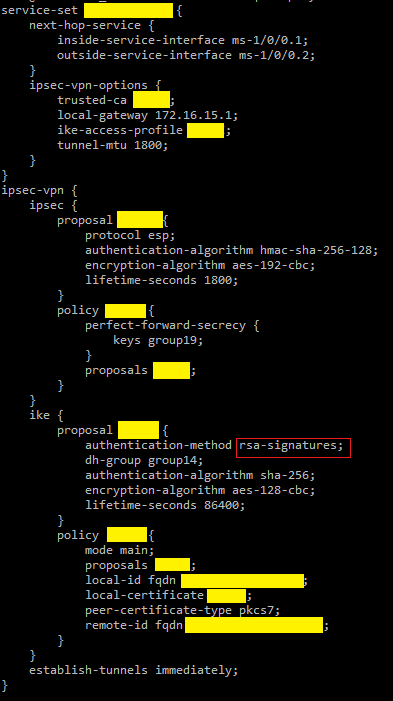
First thing you want to do is setup dynamic VPN on the MX router using RSA signature for authentication. Whether you have one, ten, or one thousand branch offices, you only need to define a single gateway in your IPSec configuration.
see sample below (had to mask some items since they are named using my customers)
First, the IPSec policies
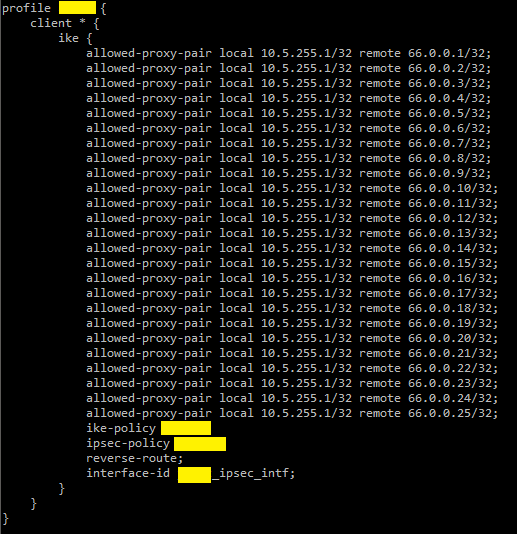
The access profile
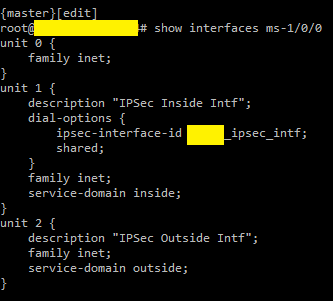
Tunnel interface
Trusted CA
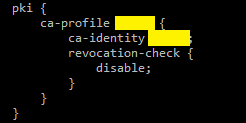
The key here is you have to have a private Certificate Authority (Windows 2016/2020 Server can be configured as one) so you can hand out digital certificates like candies to your routers.
The one I have is for a three hub MX routers with 25 branches (each branch has at least two MX peers, can be scaled to three if need be). If I need to add 10 more, all I need to add on my config is the proxy-pair pertinent to those new branches. You get the point.
The BGP configuration is the easy part. Each branch would have two BGP peers, and you can prefer one over the other via some routing policies