Three weeks ago (or a bit more depending on when you’re reading this blog) I was attending a course at Juniper's EMEA HQ in Amsterdam, together with my friend Valentijn. Ayman was teaching us about SDN in the WAN, Northstar functionality and a variety of other topics. Nice stuff to learn about. Then an e-mail arrived, sorry Ayman, I shouldn’t have read it because it distracted my attention for quite a while. Blame it on Washid, because he sent me the release notes on Junos 15.1X49-D80.4. After first glance at the release notes I couldn’t stop reading and smiling.
The list of functionalities and bug fixes was just too promising to ignore. For now, I’ll focus on what I found was most important:
- Campus and Branch - User Firewall Scale
- Remote Access Support (IPSec SSL With NCP Client) [NCP Client is supported on SRX300, SRX320, SRX340, SRX345, SRX550M, SRX550HM, SRX 1500, SRX 4100, SRX 4200 platforms only]
- Greatwall ISSU
- NGFW -- SSL Features
- Sky ATP/SSL-Proxy: Support STARTTLS used in Email Protocols
- Sky ATP/SSL-Proxy: Support SSL Reverse Proxy for Email Protocols
To many this might not look impressive. In my opinion it is. After the introduction of new hardware we now have all of the functionalities we need in a Next Generation Firewall for the branch. And yes, other brands already have them which I’m fully aware of, but many other brands don’t have the level of routing and switching support the branch SRX’s have.
So let’s take a look at the SRX at this point in time:
- Modern hardware, enough memory, Flash or SSD
- or a scalable virtual appliance on many hypervisors
- A very well accepted sandbox solution with Sky ATP
- The possibility to work with the Policy Enforcer and Space to extend policies to switch connecting the end-user.
- HTTPS (reverse) Proxy
- SSL decryption
- Workable GUI
- Central management
- User authentication against an AD controller
- UTM capabilities
Not everything is supported on the smallest hardware configuration, but from the SRX 340 and up there’s no need to worry, there’s just to think about the performance you need. To me this list makes it clear that a SRX should be on every enterprise’s shortlist when looking for a new firewall solution.
As always I discussed this with my friend Valentijn and he prefers to talk in pictures, so this is what he said to me:
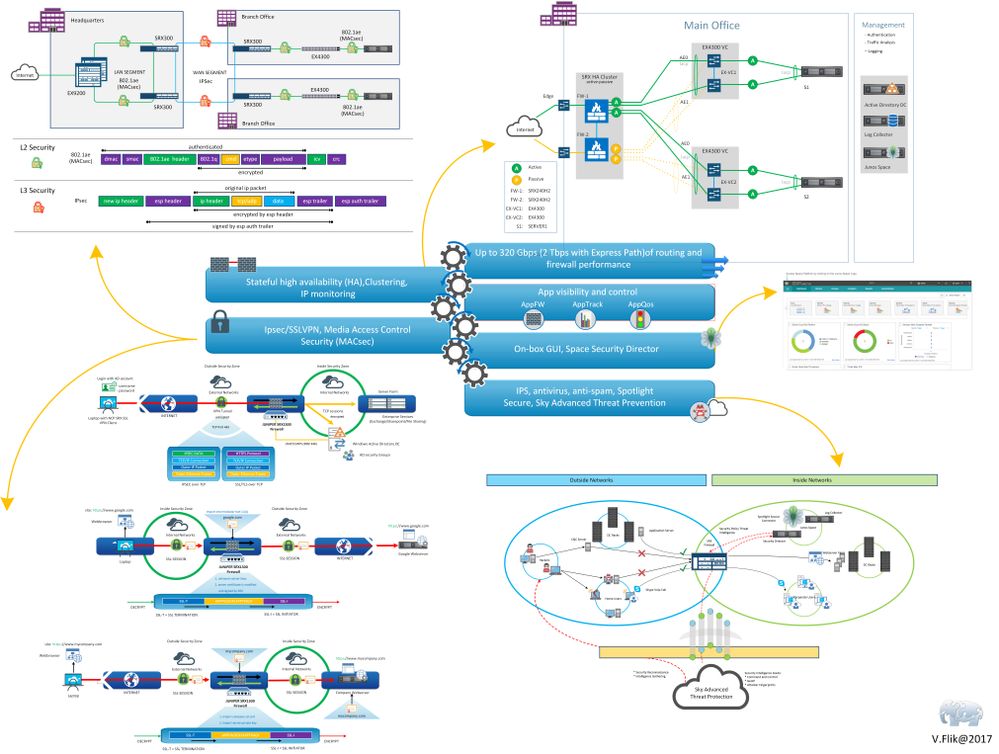
It’s safe to say that there isn’t anything missing that you need in the enterprise.
Play with it
I was able to get access to a SRX1500 to play around with it. I configured an account for SkyATP and let one classroom of the seven we have at Westcon NL use this SRX as a gateway. I know I’m a little late in testing SkyATP, but now it's done. I’m impressed with how easy it is. I configured this the week before I had to go to the Automating the WAN course. And (sorry again Ayman) another e-mail distracted my attention. The subject was “Juniper Networks Sky Advanced Threat Prevention Alert” and the mail showed:
Juniper Networks Sky Advanced Threat Prevention Alert (security realm westcon-demo):
* Threat level has changed for 172.31.3.119: 1. Host attempted to download a malicious file, sha256 checksum 3f694a42bb93be743da38e420dfd44714c7b2042dfaabb9d6110f8ec6470ef33 (score 4).
Sincerely,
Sky Advanced Threat Prevention
At first I thought something was wrong because I knew the classroom was empty during my absence. So, I looked into the Space I installed to get the details. Then it occurred to me that my colleague Jasper told me his new laptop had finally arrived. I started a chat with him (couldn’t use my phone to call him while Ayman was still teaching) and bingo, Jasper was downloading software from a site with a questionable reputation.
I performed several tests with SkyATP, but this confirmed that SkyATP does its job!
Now the next step for me was to test the two things I was interested in most: The SSL VPN and the proxy. I managed to find some time together with Jasper and we tested those functionalities. Especially on the SSL VPN the documentation could be a little better, so we had to work a few things out. That’s why we documented and published our findings on the JuniperTechWiki pages:
SSL VPN: http://forums.juniper.net/t5/Security/SSL-VPN-configuration-on-SRX-running-15-1X49-D80-4-or-higher/tac-p/306884
Proxy config: http://forums.juniper.net/t5/Security/Inspecting-outbound-HTTPS-traffic-on-Junos-15-1X49-D80-4-or/tac-p/307022
I don’t want to bore you with too many details, read the TechWiki articles when you have a chance, but we found out both functionalities work just fine!
So after all this I can draw two conclusions:
- Never read e-mail when following a course, too much distraction
- The SRX is on par with competitors and should be on every enterprise’s short list when searching for a (NG) firewall.
Things are looking good when you use the power of Junos for your security!
Everything written here is my personal view. Always check the documentation or your Juniper representative when looking for supported features.