Set Up OpenStack Firewall as a Service Plugin for SRX/vSRX
Juniper's OpenStack Neutron Plugin 2.5 has been released recently. The 2.5 release includes support for Firewall-as-a-Service for SRX and vSRX platforms. You can download the plugin and its installation instructions from Juniper’s website. In addition to configuring Juniper’s Neutron plugin, the installation process requires that you configure various Openstack operations.
In a previous article, we showed you how the FWaaS plugin handles different OpenStack operations. In this article, we show you how to set up and configure the FWaaS plugin, and the Layer 2 (VLAN) and Layer 3 (routing) plugins. A reference topology is used to walk you through the steps required to configure Openstack and Juniper’s Neutron plugin. After the installation procedure completes, you should have a working Openstack setup enabled to use Layer 2, Layer 3, and security (firewall) with Juniper’s EX/QFX switches and SRX firewalls. In addition to the configuration aspects, before using Juniper’s Neutron plugin, you must also determine how to set up and scale this infrastructure.
Installing the plugin
Download the plugin from here and install it by entering the following commands:
Ubuntu : dpkg -i python-neutron-plugin-juniper_2.5-R1-181-1_all.deb
RHEL : rpm -ivh neutron-plugin-juniper-2.5_R1_181-1.noarch.rpm
The following diagram is used as the reference topology for this article:
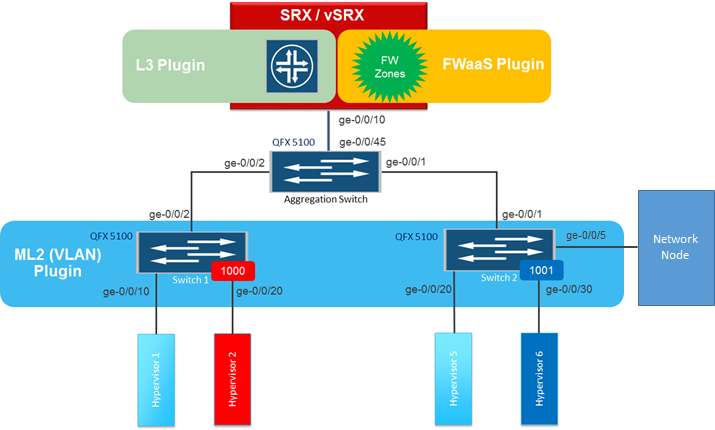
Juniper’s FWaaS plugin works in conjunction with Juniper’s Layer 2 (ML2 mechanism driver) and Layer 3 neutron plugins to create the underlying network. As a result, you should configure the Layer 2 and Layer 3 plugins before you configure the FWaaS plugin.
Initial Configuration
In the reference topology, there are three switches (Switch1, Switch2, and Aggregation Switch) and one SRX device.
- At the Aggregation Switch, set all of the necessary ports to Trunk All mode.
- Similarly, you should also set Switch1: ge-0/0/2 and Switch2: ge-0/0/1 to Trunk All mode.
- Enable vlan-tagging on the port ge-0/0/10 of the SRX
Configuring the Juniper Layer 2 (ML2) plugin
You can find the configuration information for the Juniper Layer 2 plugin here.
IMPORTANT: Before beginning the installation process, please read through the instructions and install the necessary prerequisites.
Step 1: Configuring Openstack for ML2
Configure Openstack to use VLAN type driver. On Openstack Controller, open the file /etc/neutron/neutron.conf, and update as follows:
core_plugin = neutron.plugins.ml2.plugin.Ml2Plugin
Step 2: Setting the Juniper ML2 Plugin as a mechanism driver
On Openstack Controller, update the ML2 configuration file /etc/neutron/plugins/ml2/ml2_conf.ini and set Juniper’s ML2 plugin as the mechanism driver:
[ml2]
type_drivers = vlan
mechanism_drivers = openvswitch,juniper
tenant_network_types = vlan
#additionally, mention the VLAN range and the Physical network alias to be used.
[ml2_type_vlan]
network_vlan_ranges = physnet1:1001:1200
Step 3: Adding switches to the topology
When the Juniper Plugin is installed, it supplies certain CLI commands that you can use to configure the topology. To add a device to the topology, enter the following command:
jnpr_device add -d <device_name (or) IP>
-c {switch, router, firewall}
-u <username>
-p <devicepassword>
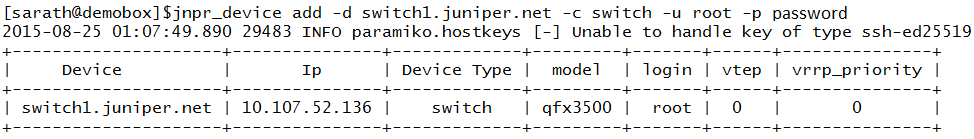
In the reference topology, the two switches (Switch1 and Switch2) are connected to the hypervisors. Enter the following statements to add and list the switches:
Adding Switch1:
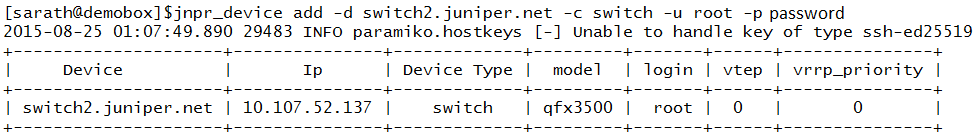
Adding Switch2:
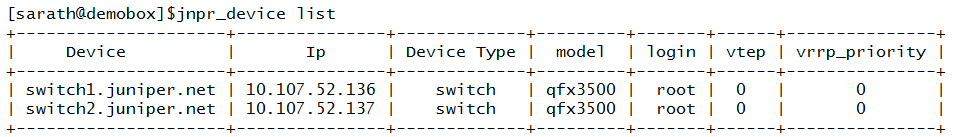
Listing the added switches:
Step 4: Defining the NIC to the physical_network mapping for each hypervisor
In OpenStack, you generally define an alias for the physical network and its associated bridge by using the following configuration in /etc/neutron/plugins/ml2/ml2_conf.ini on the NetworkNode, and for all the compute nodes:
[ovs]
tenant_network_type = vlan
bridge_mappings = physnet1:br-eth1
Because you can connect the bridge br-eth1 to any physical interface, you must add the link between the bridge br-eth1 and the physical interface to the topology by entering following command:
jnpr_nic_mapping add -H <Compute hostname>
-b <physical_network alias name>
-n NIC
Adding Hypervisor1
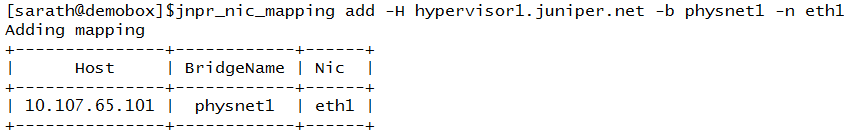
Adding Hypervisor 2
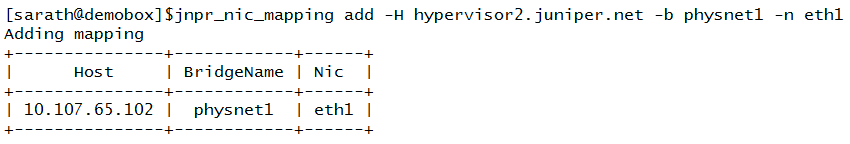
Adding Hypervisor 5 (Note that it is mapped to physnet1-- br-eth1 -- eth2)
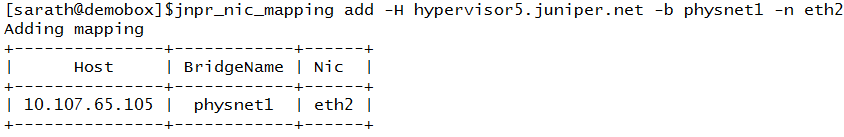
Adding Hypervisor 6
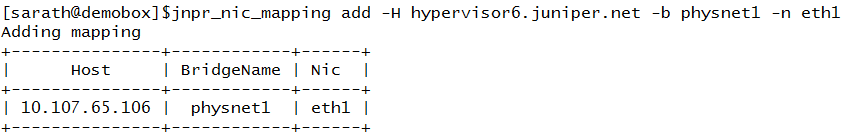
Adding Network Node
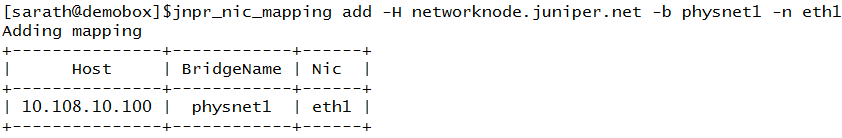
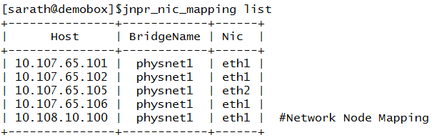
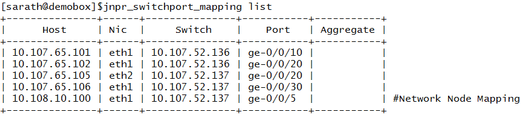
Listing all the Mappings
Step 5: Defining the mapping from the compute to the switch
To configure the VLANs on the switches, the ML2 plugin must determine the port of the switch on which the hypervisor is connected through its Ethernet interface. This provides the plugin an overall view of the topology between physnet1 -- br-eth1 -- eth1 -- Switch-x: ge-0/0/x. You can determine this information by either enabling LLDP, or by configuring it using the provided CLI. For this article, we use the provided CLI.
jnpr_switchport_mapping add -h <compute hostname>
-n NIC
-s <Switch IP/Name>
-p <Switch Port>
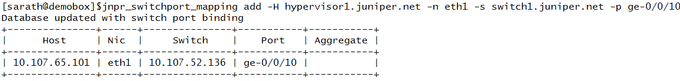
Mapping Hypervisor 1 to Switch 1
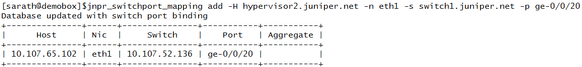
Mapping Hypervisor 2 to Switch 1
Mapping Hypervisor 5 to Switch 2

Mapping Hypervisor 6 to Switch 2
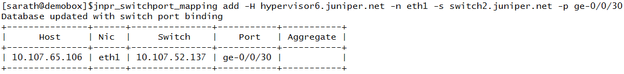
Mapping Network Node to Switch 2

Listing all the Mappings
Configuring the Neutron Layer 3 plugin
Step 1: Configuring Neutron to use Juniper’s Layer 3 service plugin
Update the Neutron configuration file /etc/neutron/neutron.conf file with the following:
service_plugins = neutron.services.juniper_l3_router.dmi.l3.JuniperL3Plugin
Step 2: Adding the router to the topology
The plugin expects the SRX device to provide both the routing and firewall services. As shown in the previous reference topology, enter the following command to add the router:
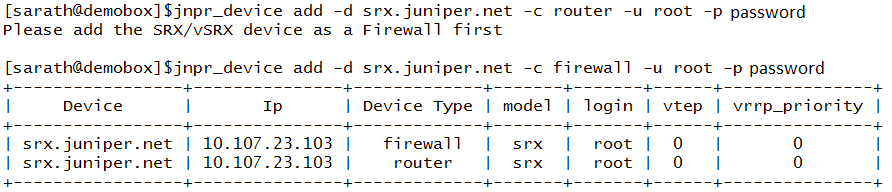
IMPORTANT: To avoid future misconfiguration issues, when you configure an SRX device as a router, you must configure it as a firewall.
Step 3: Defining the downlink port on the SRX device on which the RVI is created by the plugin
Update the plugin database with the port on the SRX device to which the Aggregation Switch is connected.
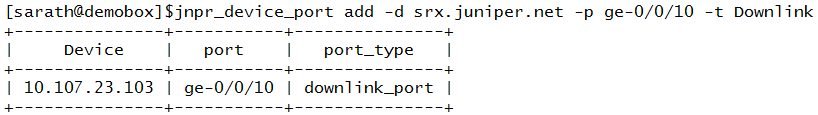
Jnpr_device_port -d <SRX device name/ip>
-p <port on the SRX>
-t <port_type: Downlink>
Adding the downlink port of the SRX device to the topology
Configuring the FWaaS plugin
To access the FWaaS plugin configuration documentation, click here.
Step 1: Configuring Neutron to use Juniper’s Layer 3 service plugin
Update the Neutron configuration file /etc/neutron/neutron.conf file with the following:
Service_plugins = neutron.services.juniper_l3_router.dmi.l3.JuniperL3Plugin,
neutron.services.juniper_fwaas.dmi.fwaas.JuniperFwaaS
Step 2: Adding the firewall to the topology
The plugin expects the SRX device to provide both the routing and firewall services. If you previously completed step 2 of Configuring the Layer 3 plugin instructions, a firewall would have already been added to the topology.
Step 3: Enabling the Horizon user interface to show the Firewall panel
To dispaly the Firewall panel under the Networks group in the Horizon user interface, open /usr/share/openstack-dashboard/openstack_dashboard/local/local_settings.py, and update the following configuration:
enable_firewall: True
After you have completed the Layer 2, Layer 3, and FWaaS plugin configurations, restart the following:
- Neutron-Server
- Ubuntu : service neutron-server restart
- CentOS : systemctl restart neutron-server
- Apache (restarts Horizon)
- Ubuntu : service apache2 restart
- CentOS : systemctl restart httpd
You should now have a fully functioning installation with Juniper’s Layer 2 mechanism driver, Layer 3, and FWaaS plugins successfully configured. For any questions or for more information, contact the plugin team on quantum-plugin-support quantum-plugin-support@juniper.net.