Dear Expert,
I have a problem with Segment Routing for Legacy LFA. Backup Path calculates the problem. The topology diagram is as follows:
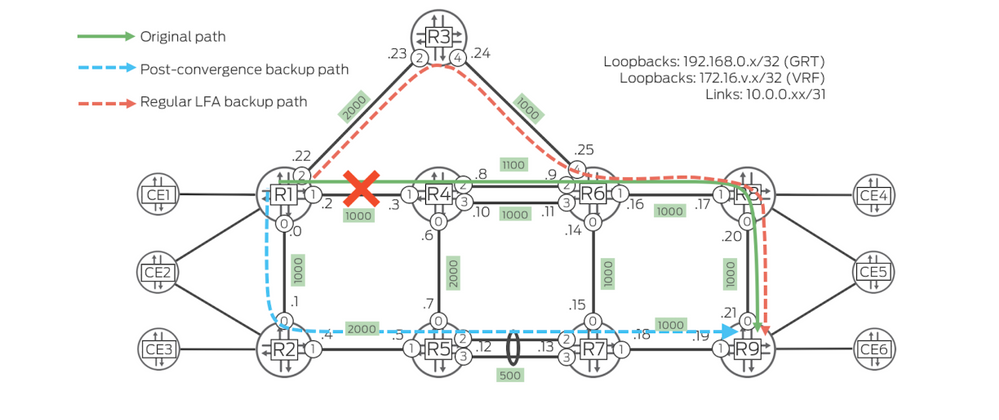
Currently, the routing table inet.3 from R1 to R9.
[edit]
jcluser@R1# show protocols mpls |display set
Jun 06 10:46:52
set protocols mpls icmp-tunneling
set protocols mpls interface ge-0/0/0.0
set protocols mpls interface ge-0/0/1.0
set protocols mpls interface ge-0/0/2.0
set protocols mpls label-range static-label-range 10000 20000
[edit]
jcluser@R1# show protocols isis | display set
Jun 06 10:46:55
set protocols isis apply-groups gr-isis
set protocols isis reference-bandwidth 1000g
set protocols isis backup-spf-options remote-backup-calculation
set protocols isis backup-spf-options node-link-degradation
set protocols isis backup-spf-options use-source-packet-routing
set protocols isis source-packet-routing srgb start-label 1000
set protocols isis source-packet-routing srgb index-range 9000
set protocols isis source-packet-routing node-segment ipv4-index 401
set protocols isis source-packet-routing node-segment ipv6-index 601
set protocols isis level 2 wide-metrics-only
set protocols isis interface ge-0/0/1.0 node-link-protection
set protocols isis interface ge-0/0/1.0 level 2 lan-neighbor 0000.0000.0002 ipv4-adjacency-segment protected index 100
set protocols isis interface ge-0/0/2.0 point-to-point
set protocols isis interface ge-0/0/2.0 node-link-protection
set protocols isis interface ge-0/0/2.0 level 2 metric 2000
set protocols isis interface ge-0/0/2.0 level 2 ipv4-adjacency-segment unprotected dynamic
set protocols isis interface ge-0/0/2.0 level 1 disable
set protocols isis interface all node-link-protection
set protocols isis interface all level 1 disable
jcluser@R1# run show route table inet.3 192.168.0.9/32
Jun 06 10:47:51
inet.3: 9 destinations, 9 routes (9 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
192.168.0.9/32 *[L-ISIS/14] 00:16:54, metric 4000
> to 10.0.0.3 via ge-0/0/0.0, Push 1409
to 10.0.0.23 via ge-0/0/2.0, Push 1409
jcluser@R1# run show route table inet.3 detail 192.168.0.9 | match "entry|L-ISIS|weight|operation"
Jun 06 10:48:42
192.168.0.9/32 (1 entry, 1 announced)
*L-ISIS Preference: 14
Next hop: 10.0.0.3 via ge-0/0/0.0 weight 0x1, selected
Label operation: Push 1409
Next hop: 10.0.0.23 via ge-0/0/2.0 weight 0xf000
Label operation: Push 1409
[edit]
jcluser@R1# run show route forwarding-table destination 192.168.0.9/32
Jun 06 10:49:15
Routing table: default.inet
Internet:
Enabled protocols: Bridging,
Destination Type RtRef Next hop Type Index NhRef Netif
192.168.0.9/32 user 0 ulst 1048582 16
10.0.0.3 ucst 610 16 ge-0/0/0.0
10.0.0.23 ucst 605 12 ge-0/0/2.0
The first question: R1 to R9 I have already based load balancing on the packet, and also have two next hop addresses in the forwarding table. The routing table inet.3 shows the selected R4 as the next hop. If the traffic reaches 192.168.0.9, will it pass the address 10.0.0.23?
The second question: R3 I have set the interface to an unprotected state. When R1 calculates the backup path, R3 should not be selected. But it seems that the route seems to have chosen R3.
[edit]
jcluser@R3# show protocols isis | display set
set protocols isis export isis-expoert
set protocols isis reference-bandwidth 1000g
set protocols isis source-packet-routing srgb start-label 1000
set protocols isis source-packet-routing srgb index-range 9000
set protocols isis source-packet-routing node-segment ipv4-index 403
set protocols isis source-packet-routing node-segment ipv6-index 603
set protocols isis level 2 wide-metrics-only
set protocols isis interface ge-0/0/1.0 point-to-point
set protocols isis interface ge-0/0/1.0 level 2 ipv4-adjacency-segment unprotected dynamic
set protocols isis interface ge-0/0/2.0 point-to-point
set protocols isis interface ge-0/0/2.0 node-link-protection
set protocols isis interface ge-0/0/2.0 level 2 metric 2000
set protocols isis interface ge-0/0/2.0 level 2 ipv4-adjacency-segment unprotected dynamic
set protocols isis interface ge-0/0/2.0 level 2 ipv6-adjacency-segment unprotected dynamic
set protocols isis interface ge-0/0/2.0 level 1 disable
set protocols isis interface all level 1 disable
set protocols isis interface all level 2 ipv4-adjacency-segment unprotected dynamic
[edit]
jcluser@R3# run show isis adjacency detail
R6
Interface: ge-0/0/1.0, Level: 2, State: Up, Expires in 20 secs
Priority: 0, Up/Down transitions: 1, Last transition: 00:22:33 ago
Circuit type: 3, Speaks: IP, IPv6
Topologies: Unicast
Restart capable: Yes, Adjacency advertisement: Advertise
IP addresses: 10.0.0.25
IPv6 addresses: fe80::250:56ff:fea2:755a
Level 2 IPv4 unprotected Adj-SID: 18, Flags: --VL--
R1
Interface: ge-0/0/2.0, Level: 2, State: Up, Expires in 26 secs
Priority: 0, Up/Down transitions: 1, Last transition: 00:22:57 ago
Circuit type: 2, Speaks: IP, IPv6
Topologies: Unicast
Restart capable: Yes, Adjacency advertisement: Advertise
IP addresses: 10.0.0.22
IPv6 addresses: fe80::250:56ff:fea2:c0d7
Level 2 IPv4 unprotected Adj-SID: 16, Flags: --VL--
Level 2 IPv6 unprotected Adj-SID: 17, Flags: F-VL--
Is it that I understand the problem with the protection mechanism? Or have an official description. thank.